+49 800 / 27 00 001
We are thrilled to serve you
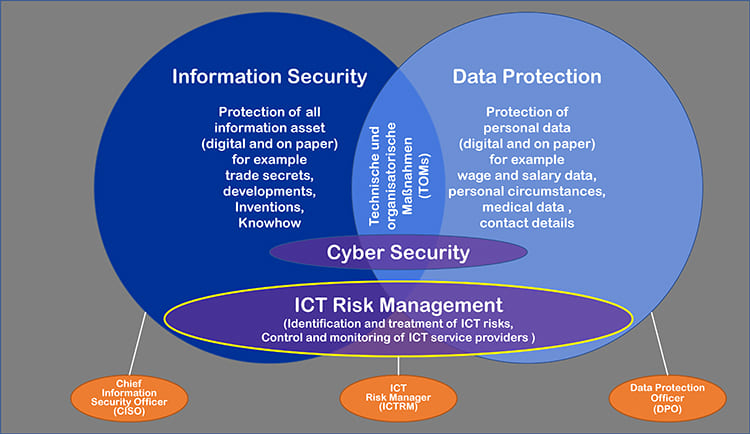
Individual advice in the area of ICT risk management
The following topics need to be considered in the context of ICT risk management, where we can advise and support you with our specialist expertise:
- Governance and organization
- Risk management strategy: Development and implementation of a comprehensive risk management strategy that meets the requirements of DORA.
- Organizational structures: Establishment of clear organizational structures and responsibilities for ICT risk management.
- Continuous monitoring: Implementation of processes for the continuous monitoring and assessment of ICT risks.
- Identification and assessment of risks
- Risk assessment: Regular performance of risk assessments to identify potential threats and vulnerabilities in ICT systems.
- Threat analysis: Analyzing current and emerging cyber threats and their potential impact on operational resilience.
- Vulnerability management: Identification and elimination of vulnerabilities in IT systems and infrastructures.
- Risk mitigation and controls
- Security controls: Implementation of technical and organizational measures to mitigate identified risks.
- Access controls: Establishing and managing secure access controls to prevent unauthorized access to critical systems.
- Data encryption: Use of encryption technologies to protect sensitive data.
- Monitoring and detection
- Network monitoring: Implementing systems to monitor the network and detect suspicious activity.
- Intrusion detection systems (IDS): Use of IDS for early detection of cyber attacks.
- Anomaly detection: Use of techniques to detect unusual activities that could indicate potential security incidents.
- Incident response and contingency planning
- Incident response: Development and implementation of incident response plans to respond effectively to security incidents.
- Contingency plans: Creation and regular review of contingency plans to ensure operational capability in the event of a cyber attack.
- Disaster recovery: Development of strategies and measures to restore critical systems and data after an incident.
- Testing and validation
- Penetration tests: Regularly carrying out penetration tests to check the security of systems and identify vulnerabilities.
- Security audits: Conducting regular security audits and security compliance reviews.
- Simulations: Conducting simulations and exercises to assess cyber incident response capabilities.
- Training and awareness
- Employee training: Conduct regular training for employees to raise awareness of cyber risks and security policies.
- Awareness creation: Implementation of programs to create awareness of cybersecurity and promote security-conscious behavior.
- Supplier and third-party management
- Supplier assessment: Assessing the cyber risks posed by suppliers and third parties.
- Contract management: Implementation of security requirements in contracts with suppliers and third parties.
- Monitoring: Continuous monitoring of compliance with security requirements by suppliers and third parties.
- Reporting and documentation
- Documentation: Maintaining comprehensive documentation of all ICT risk management activities, including risk assessments, measures and incidents.
- Reporting: Regular reporting to management and relevant regulators on the status of digital resilience and any incidents.
- Compliance and regulatory requirements
- Regulatory compliance: Ensuring compliance with all relevant legal and regulatory requirements, including the requirements of DORA.
- Audits and reviews: Preparation for audits and reviews by regulators and independent auditors.

Our consulting approach aims to take a holistic view of any organizational structure and form. We contribute our expertise and proven best practice approaches to the implementation of your ICT risk management in particular. We also develop pragmatic solutions for you.
We would be happy to provide you with information in an initial free and non-binding consultation.



